
A malicious app downloaded from Google Play more than 10,000 times surreptitiously installed a remote access trojan that stole users’ passwords, text messages, and other confidential data, a security firm reported.
The trojan, which goes under the names TeaBot and Anatsa, came to light last May. It used streaming software and abused Android’s accessibility services in a way that allowed the malware creators to remotely view the screens of infected devices and interact with the operations the devices carried out. At the time, TeaBot was programmed to steal data from a predefined list of apps from about 60 banks around the world.
On Tuesday, security firm Cleafy reported that TeaBot was back. This time, the trojan spread through a malicious app called QR Code & Barcode Scanner, which as the name suggests, allowed users to interact with QR codes and barcodes. The app had more than 10,000 installations before Cleafy researchers notified Google of the fraudulent activity and Google removed it.
“One of the biggest difference[s], compared to the samples discovered during… May 2021, is the increase of targeted applications which now include home banking applications, insurances applications, crypto wallets, and crypto exchanges,” Cleafy researchers wrote. “In less than a year, the number of applications targeted by TeaBot have grown more than 500%, going from 60 targets to over 400.”
In recent months, TeaBot also started supporting new languages including Russian, Slovak, and Mandarin Chinese to display custom messages on infected phones. The fraudulent scanner app distributed on Play was detected as malicious by only two antimalware services, and it requested only a few permissions at the time it was downloaded. All the reviews portrayed the app as legitimate and well-functioning, making TeaBot harder for less experienced people to recognize as a risk.
Once installed, the malicious QR Code & Barcode Scanner app displayed a pop-up informing users that an update was available. But rather than making the update available through Play as is normal, the pop-up downloaded it from two specific GitHub repositories created by a user named feleanicusor. The two repositories, in turn, installed TeaBot.
This graph gives an overview of the infection chain developed by the TeaBot authors:
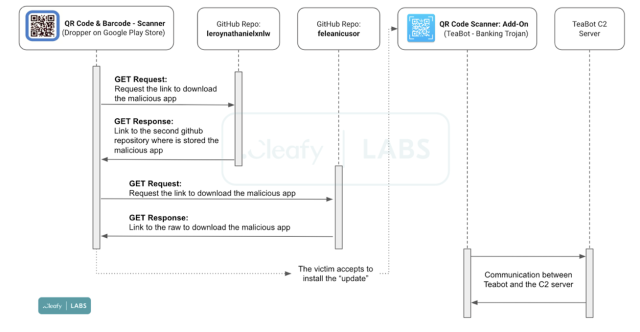
Cleafy researchers wrote:
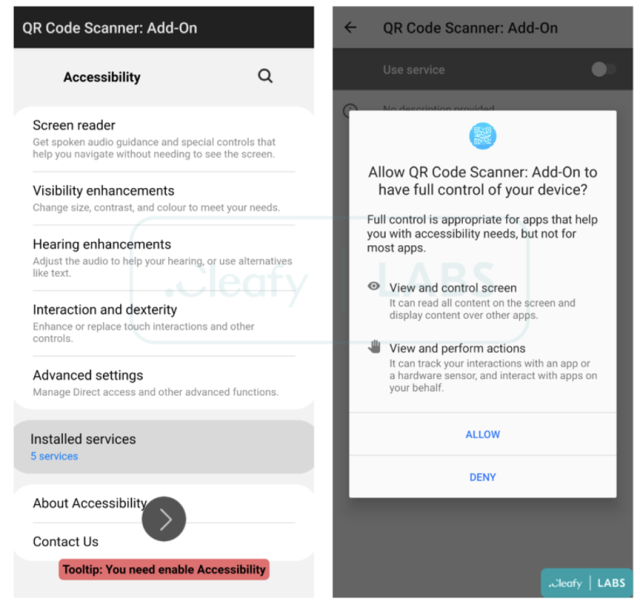
Once the users accept to download and execute the fake “update”, TeaBot will start its installation process by requesting the Accessibility Services permissions in order to obtain the privileges needed:
- View and control screen: used for retrieving sensitive information such as login credentials, SMS, 2FA codes from the device’s screen.
- View and perform actions: used for accepting different kinds of permissions, immediately after the installation phase, and for performing malicious actions on the infected device.
TeaBot is only the latest piece of Android malware to be spread through Google’s official app market. The company is generally quick to remove malicious apps once they’re reported, but it continues to struggle to identify malware on its own. Google representatives didn’t respond to an email seeking comment for this post.
Tuesday’s post from Cleafy has a list of indicators that people can use to determine if they installed the malicious app.
Listing image by Getty Images