
The Brave browser will take action against websites that snoop on visitors by scanning their open Internet ports or accessing other network resources that can expose personal information.
Starting in version 1.54, Brave will automatically block website port scanning, a practice that a surprisingly large number of sites were found engaging in a few years ago. According to this list compiled in 2021 by a researcher who goes by the handle G666g1e, 744 websites scanned visitors’ ports, most or all without providing notice or seeking permission in advance. eBay, Chick-fil-A, Best Buy, Kroger, and Macy’s were among the offending websites.
Some sites use similar tactics in an attempt to fingerprint visitors so they can be re-identified each time they return, even if they delete browser cookies. By running scripts that access local resources on the visiting devices, the sites can detect unique patterns in a visiting browser. Sometimes there are benign reasons a site will access local resources, such as detecting insecurities or allowing developers to test their websites. Often, however, there are more abusive or malicious motives involved.
The new version of Brave will curb the practice. By default, no website will be able to access local resources. More advanced users who want a particular site to have such access can add it to an allow list. The interface will look something like the screenshot displayed below.
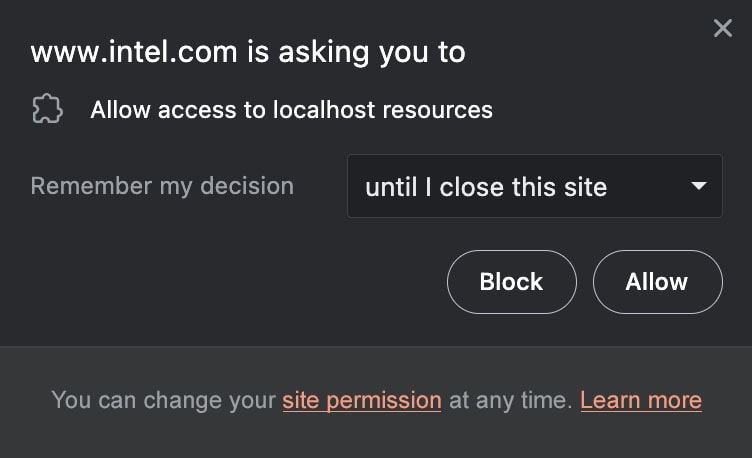
Brave will continue to use filter list rules to block scripts and sites known to abuse localhost resources. Additionally, the browser will include an allow list that gives the green light to sites known to access localhost resources for user-benefiting reasons.
“Brave has chosen to implement the localhost permission in this multistep way for several reasons,” developers of the browser wrote. “Most importantly, we expect that abuse of localhost resources is far more common than user-benefiting cases, and we want to avoid presenting users with permission dialogs for requests we expect will only cause harm.”
The scanning of ports and other activities that access local resources is typically done using JavaScript that’s hosted on the website and runs inside a visitor’s browser. A core web security principle known as the same origin policy bars JavaScript hosted by one Internet domain from accessing the data or resources of a different domain. This prevents malicious Site A from being able to obtain credentials or other personal data associated with Site B.
The same origin policy, however, doesn’t prevent websites from interacting in some ways with a visitor’s localhost IP address of 127.0.0.1. Summarizing this writeup from security firm Forcepoint, Wikipedia writers explain why:
Even when same-origin policy is in effect (without being relaxed by Cross-Origin Resource Sharing), certain cross-origin computer attacks can be performed. WebRTC can be used to find out the internal IP address of a victim. If attempting to connect to a cross-origin port, responses cannot be read in face of same-origin policy, but a JavaScript can still make inferences on whether the port is open or closed by checking if the onload/onerror event fires, or if we get a timeout. This gives opportunities for cross-origin portscanning. Further, a JavaScript can even fingerprint services cross-origin by taking advantage of default files. For example, if a JavaScript loaded from the site evil.com attempts to open the file http://127.0.0.1/images/jenkins.png, and the onload event fires, then it can be inferred that the victim runs Jenkins on their own computer. This way, the attacker can find potentially vulnerable services for example on the internal network, even in face of same-origin policy. Should any service be vulnerable to Cross-site Request Forgery, they can even be compromised.
This form of cross-origin access has existed as long as the web has. While Brave said that Apple’s Safari browser has blocked some forms of localhost access, it doesn’t block all of them. Various browser extensions also block such access.
“As far as we can tell, Brave is the only browser that will block requests to localhost resources from both secure and insecure public sites, while still maintaining a compatibility path for sites that users trust (in the form of the discussed localhost permission)” the Brave post said.
The browser developer added:
Thanks to this historical “accident,” a small but important amount of software has been built expecting to be freely accessible by websites, often in ways invisible to users. And many of these uses are benign. Examples include some wallets for cryptocurrencies, security software provided by banks or security companies, and hardware devices that use certain Web interfaces for configuration.
In some situations, browsers also allow public websites to access localhost resources to help developers test their software.
Unfortunately, a wide range of malicious, user-harming software on the Web uses access to localhost resources for malicious reasons. For example, fingerprinting scripts try to detect unique patterns in the other software you have running on your device to re-identify you, and other scripts try to identify insecure and vulnerable software on the machine and try to exploit it.
Post updated to correct details about limitations of the same origin policy.