A federal Cyber Safety Review Board has issued its report on what led to last summer’s capture of hundreds of thousands of emails by Chinese hackers from cloud customers, including federal agencies. It cites “a cascade of security failures at Microsoft” and finds that “Microsoft’s security culture was inadequate” and needs to adjust to a “new normal” of cloud provider targeting.
The report, mandated by President Biden in the wake of the far-reaching intrusion, details the steps that Microsoft took before, during, and after the breach and in each case finds critical failure. The breach was “preventable,” even though it cites Microsoft as not knowing precisely how Storm-0558, a “hacking group assessed to be affiliated with the People’s Republic of China,” got in.
“Throughout this review, the board identified a series of Microsoft operational and strategic decisions that collectively points to a corporate culture that deprioritized both enterprise security investments and rigorous risk management,” the report reads.
The report notes that Microsoft “fully cooperated with the Board’s review.” A Microsoft spokesperson issued a statement regarding the report. “We appreciate the work of the CSRB to investigate the impact of well-resourced nation state threat actors who operate continuously and without meaningful deterrence,” the statement reads. “As we announced in our Secure Future Initiative, recent events have demonstrated a need to adopt a new culture of engineering security in our own networks.” Along with hardening its systems and implementing more sensors and logs to “detect and repel the cyber-armies of our adversaries,” Microsoft said it would “review the final report for additional recommendations.”
“Inaccurate public statements” and unsolved mysteries
The Cyber Safety Review Board (CSRB), formed two years ago, is composed of government and industry officials, from entities including the Departments of Homeland Security, Justice, and Defense, the NSA, FBI, and others. Microsoft provides cloud-based services, including Exchange and Azure, to numerous government agencies, including consulates.
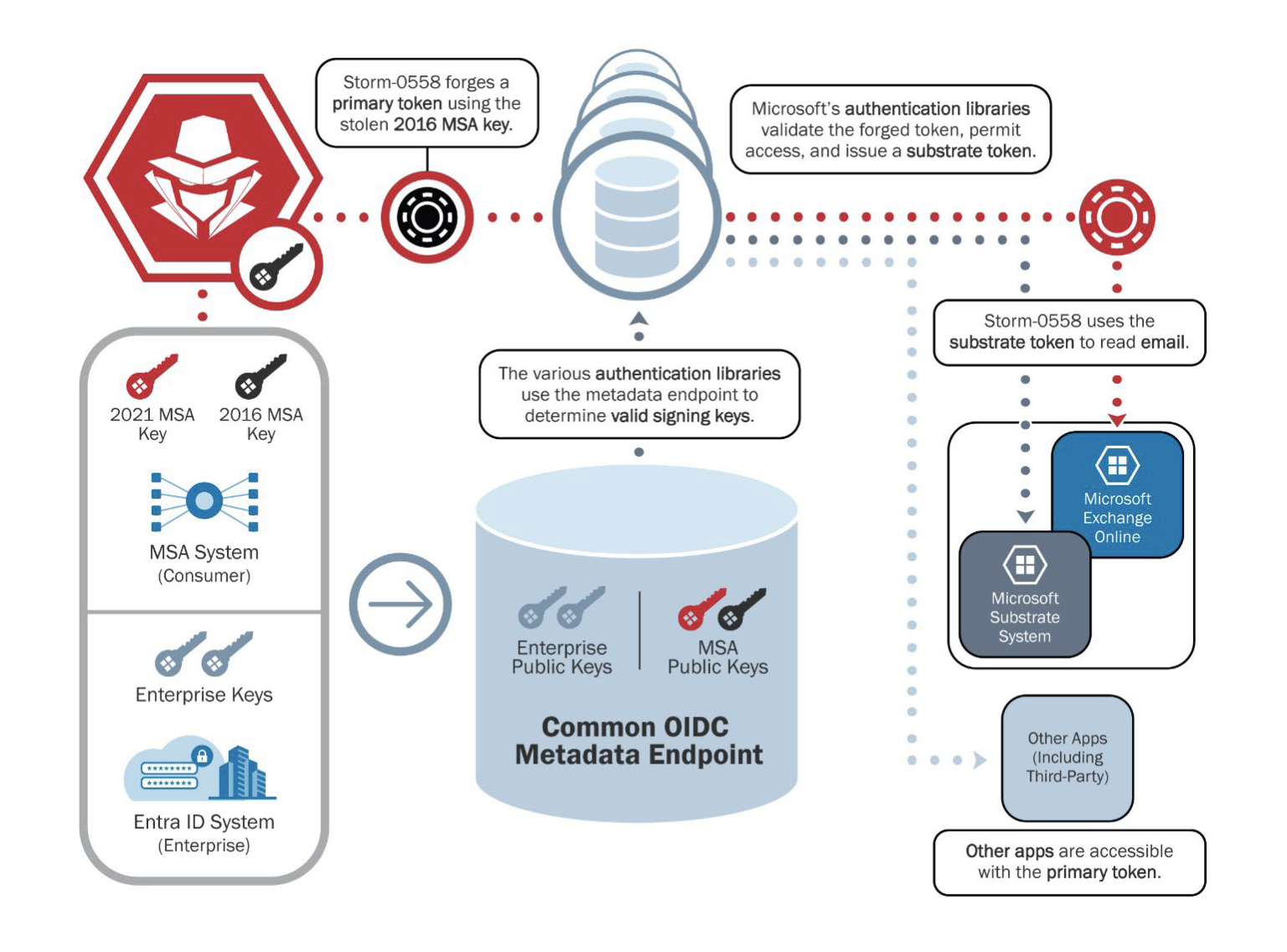
Microsoft has previously offered a version of the intrusion story, one that notably avoids the words “vulnerability,” “exploit,” or “zero-day.” A Microsoft post in July 2023 cited an inactive signing key acquired by Storm-0558, which was then used to forge tokens for the Azure AD cloud service that stores keys for logins. This was “made possible by a validation error in Microsoft code,” Microsoft wrote.
Congress and government agencies called on Microsoft to offer far more disclosure, and others, including Tenable’s CEO, offered even harsher assessments. In September, the company met them partway. It was an engineer’s account that was hacked, Microsoft claimed, giving attackers access to a supposedly locked-down workstation, the consumer signing key, and, crucially, access to crash dumps moved into a debugging environment. A “race condition” prevented a mechanism that strips out signing keys and other sensitive data from crash dumps from functioning. Furthermore, “human errors” allowed for an expired signing key to be used in forging tokens for modern enterprise offerings.
Those kinds of unrevealing, withholding public statements were cited by the CSRB in its finding of Microsoft’s failures. The report cites “Microsoft’s decision not to correct, in a timely manner, its inaccurate public statements about this incident, including a corporate statement that Microsoft believed it had determined the likely root cause of the intrusion when in fact, it still has not.” It also notes that Microsoft did not update its September 2023 blog post about the invasion cause until March 2024, “as the Board was concluding its review and only after the Board’s repeated questioning about Microsoft’s plans to issue a correction.” (The updated blog post notes that Microsoft has “not found a crash dump containing the impacted key material.”)